1. keepalived模式
1.1. 双主模式
应对高并发的时候设置的双主模式. 拆分域名.
vrrp_instance vip_10.0.0.4 {
state BACKUP
interface ens33
virtual_router_id 61
priority 50
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
10.0.0.4 dev ens33 label ens33:2
}
}
vrrp_instance vip_10.0.0.4 {
state MASTER
interface ens33
virtual_router_id 61
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
10.0.0.4 dev ens33 label ens33:2
}
}
1.2. 非抢占模式
keepalived 主备默认是抢占式,主挂了,备接管.主恢复,不希望主重新抢回资源
state BACKUP
nopreemptvrrp_instance vip_10.0.0.3 {
state BACKUP
nopreempt
interface ens33
virtual_router_id 51
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
10.0.0.3 dev ens33 label ens33:1
}
}
2. HTTP证书
2.1. https概述
https == http over tls
- 基于http协议,传输的时候进行加密.
- 如果不使用https,数据传输都是明文的.
应用场景:
- 目前大部分的业务都是使用https加密.
- 企业想使用http 2.0基于https.
2.2. 部署https加密的流程
- 域名 *.jd.com www.jd.com
- 根据域名申请https证书(私钥与公钥(ca证书)),自己创建. (免费的https证书3个月有效期)
- 进行配置web/lb进行配置..
- 跳转http-->https
- 监控
2.3. Https加密流程(单台)web
[root@web01 /etc/nginx]# cat /etc/nginx/conf.d/ssl.oldboylinux.cn.conf
server {
listen 443 ssl;
server_name ssl.oldboylinux.cn;
root /app/code/ssl;
ssl_certificate /etc/nginx/ssl_keys/ssl.oldboylinux.cn.pem;
ssl_certificate_key /etc/nginx/ssl_keys/ssl.oldboylinux.cn.key;
location / {
index index.html;
}
}
mkdir -p /etc/nginx/ssl_keys/
uzip 15697758_ssl.oldboylinux.cn_nginx.zip
mkdir -p /app/code/ssl
echo ssl > /app/code/ssl/index.html2.4. http跳转https
[root@web01 /etc/nginx]# cat /etc/nginx/conf.d/ssl.oldboylinux.cn.conf
server {
listen 80;
server_name ssl.oldboylinux.cn;
return 302 https://ssl.oldboylinux.cn$request_uri;
}
server {
listen 443 ssl;
server_name ssl.oldboylinux.cn;
root /app/code/ssl;
ssl_certificate /etc/nginx/ssl_keys/ssl.oldboylinux.cn.pem;
ssl_certificate_key /etc/nginx/ssl_keys/ssl.oldboylinux.cn.key;
location / {
index index.html;
}
}2.5. https认证原理
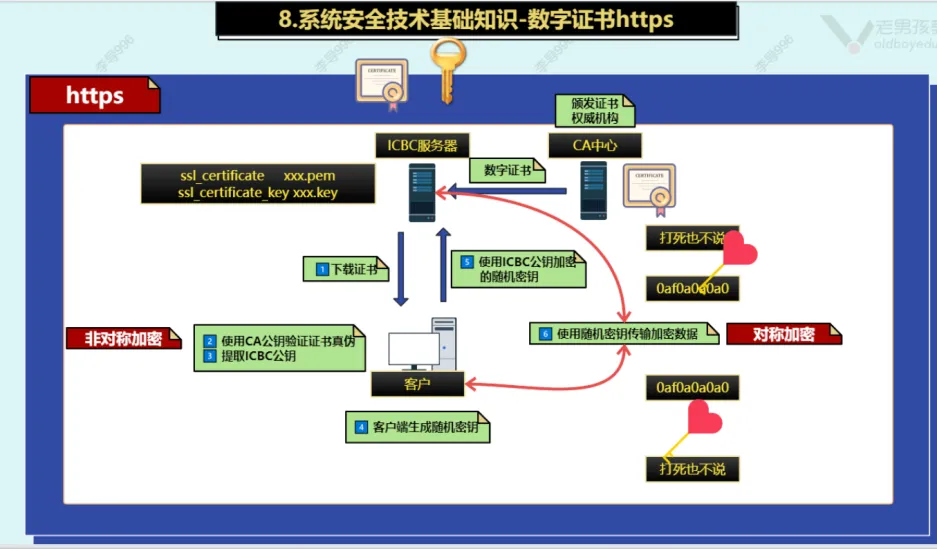
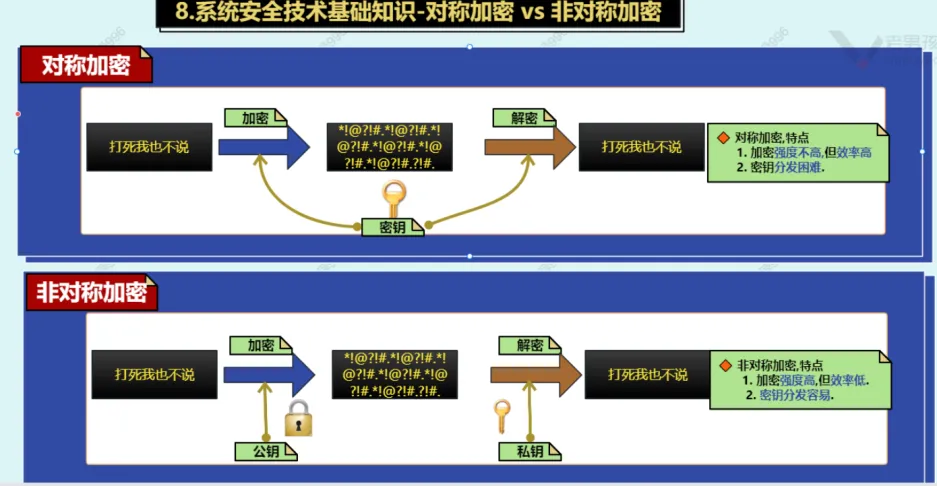
2.6. 命令行创建https证书(自己给自己颁发证书)
#创建私钥 私钥server.key
openssl genrsa -idea -out server.key 2048
#根据私钥创建 证书 server.crt .pem证书
openssl req -days 36500 -x509 -sha256 -nodes -newkey rsa:2048 - keyout server.key -out server.crt3. 网站集群https配置
| 配置思路 | |
| 全部进行加密 | 用户-🔐->lb-->🔐web |
| 部分加密 | 用户-🔐->lb-->web |
老男孩教育-最新架构-集群与https| ProcessOn免费在线作图,在线流程图,在线思维导图
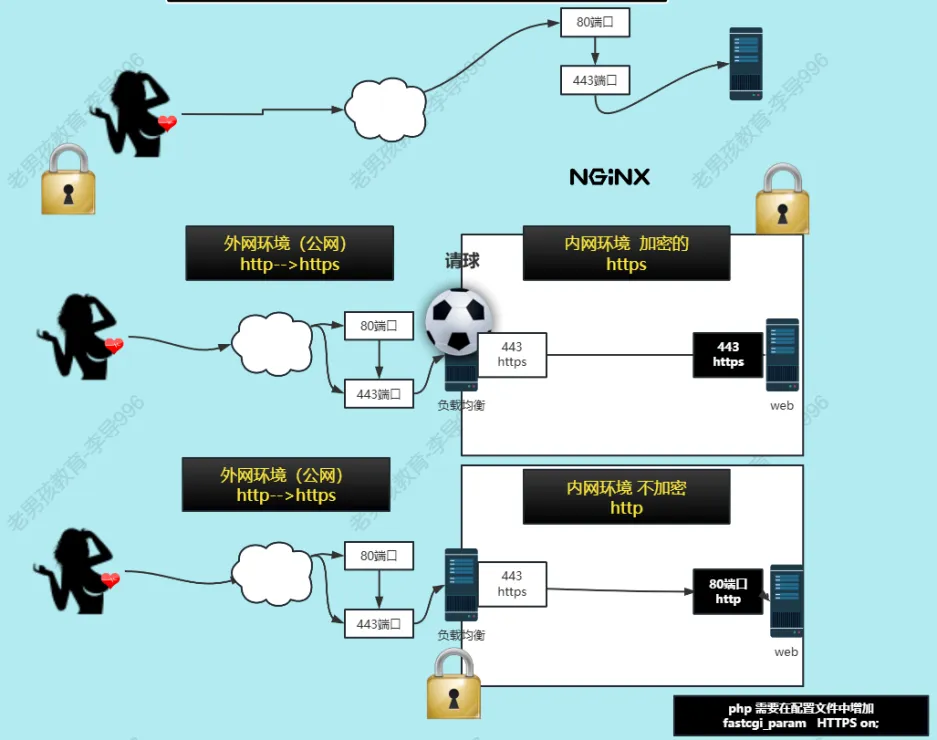
3.1. web
[root@web01 ~]# cat /etc/nginx/conf.d/blog.weiwei666.cn.conf
server {
listen 443 ssl;
server_name blog.weiwei666.cn;
root /app/code/blog;
error_log /var/log/nginx/blog.weiwei666.cn-error.log notice;
access_log /var/log/nginx/blog.weiwei666.cn-access.log main;
ssl_certificate /etc/nginx/ssl_keys/blog.weiwei666.cn.pem;
ssl_certificate_key /etc/nginx/ssl_keys/blog.weiwei666.cn.key;
location / {
index index.php;
}
location ~* \.php {
if ( $http_user_agent ~ "lb_check") {
access_log off;
}
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include fastcgi_params;
}
}
3.2. lb
[root@lb01 /etc/nginx/conf.d]# cat lb-blog.weiwei666.cn.conf
upstream blog_pools {
server 10.0.0.7:443;
server 10.0.0.8:443;
}
server {
listen 80;
server_name blog.weiwei666.cn;
return 302 https://blog.weiwei666.cn$request_uri;
}
server {
listen 443 ssl;
server_name blog.weiwei666.cn;
error_log /var/log/nginx/blog.weiwei666.cn-error.log notice;
access_log /var/log/nginx/blog.weiwei666.cn-access.log main;
ssl_certificate /etc/nginx/ssl_keys/blog.weiwei666.cn.pem;
ssl_certificate_key /etc/nginx/ssl_keys/blog.weiwei666.cn.key;
location / {
proxy_pass https://blog_pools;
proxy_set_header Host $http_host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Real-Ip $remote_addr;
}
}
3.3. keepalived——lb主
[root@lb01 /etc/nginx/conf.d]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
router_id lb01
}
#定义监控脚本
vrrp_script check_ngx.sh {
script /server/scripts/check_ngx.sh
interval 2
weight 1
user root
}
vrrp_instance vip_10.0.0.3 {
state MASTER
interface ens33
virtual_router_id 51
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
10.0.0.3 dev ens33 label ens33:1
}
#这个vrrp实例使用check_ngx.sh脚本
track_script {
check_ngx.sh
}
}
3.4. keepalived——lb副
[root@lb02 /etc/nginx/conf.d]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
router_id lb02
}
vrrp_instance vip_10.0.0.3 {
state BACKUP
interface ens33
virtual_router_id 51
priority 50
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
10.0.0.3 dev ens33 label ens33:1
}
}
3.5. hosts解析
10.0.0.3 blog.weiwei666.cn3.6. 访问页面
blog.weiwei666.cn